The EU framework for digital wallets and technical requirements
This article is an adaptation of our previously published technical deep-dive on WSCD/WSCA implementation options, simplified to focus on organizational considerations rather than technical specifications.
The European Union is establishing a comprehensive framework for digital identity through the eIDAS 2.0 regulation. At the heart of this initiative is the Architectural Reference Framework (ARF), currently in version 1.4, which defines the technical specifications and security requirements that organizations must follow when implementing digital identity wallets.
For organizations developing or deploying wallet solutions, one of the most significant requirements appears in Topic 16 of Annex 2 in the ARF. This section mandates that wallet providers ensure their solutions can generate Qualified Electronic Signatures (QES), which carry the same legal weight as handwritten signatures across the EU. Your implementation must support the generation of these signatures through either local or remote signing applications, making your choice of security architecture particularly consequential.
Understanding the technical foundation of compliant wallet solutions is essential. The ARF specifies that every digital wallet implementation consists of two fundamental components that work in tandem:
- The Wallet Instance (WI), or the user-facing app: This is the mobile application that users directly interact with – essentially the front-end interface of your solution. This component handles user interactions, displays credentials, and facilitates verification processes.
- The secure storage and processing system: This critical backend consists of two interconnected elements:
- Wallet Secure Cryptographic Device (WSCD): This component provides the protected hardware environment where sensitive cryptographic operations occur. It functions as a secure vault for digital identity credentials, ensuring these assets remain protected from unauthorized access or duplication.
- Wallet Secure Cryptographic Application (WSCA): This component manages all cryptographic operations within the secure environment. It controls access to private keys, handles credential management, and executes operations like digital signing.
These components communicate through a Secure Cryptographic Interface (SCI), which ensures that all sensitive operations occur within protected channels. This comprehensive security architecture safeguards the entire credential lifecycle, from issuance through verification.
The ARF’s technical specifications recognize that organizations have different requirements, capabilities, and implementation constraints. Therefore, it identifies four distinct approaches for implementing this secure storage architecture. Your choice among these options will profoundly influence your deployment strategy, user experience, operational costs, and scalability potential.
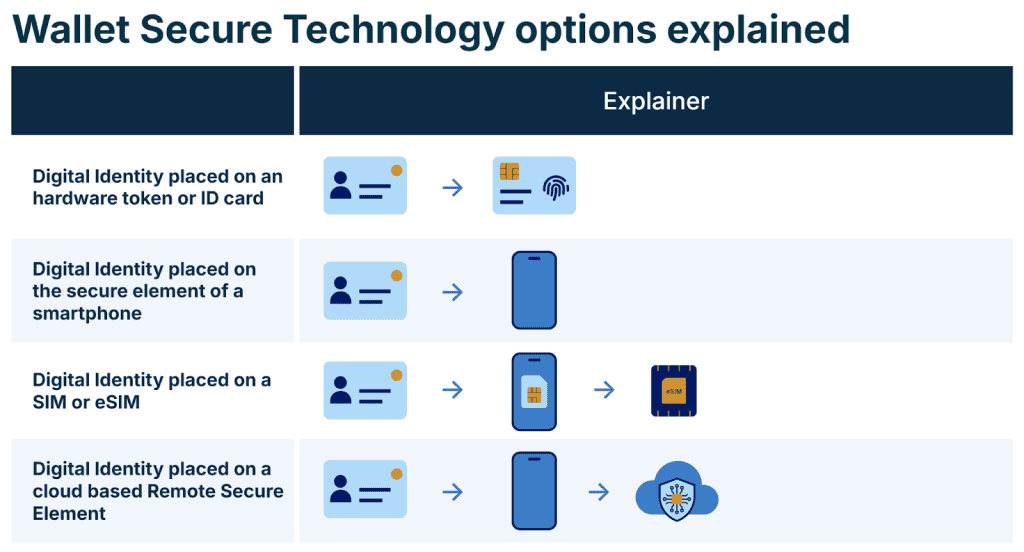
The four implementation options for secure digital wallet storage
1. Digital identity on hardware tokens or ID cards (Local External WSCD/WSCA)
This implementation utilizes external hardware devices specifically designed for cryptographic operations. These physical devices – such as hardware security tokens, USB tokens, or smart ID cards – provide a physically separate secure environment for digital identity credentials.
How the technology works
In this approach, the external hardware device serves as both the Wallet Secure Cryptographic Device (WSCD) and hosts the Wallet Secure Cryptographic Application (WSCA). The device is physically separate from the smartphone, creating hardware isolation for sensitive operations. When cryptographic functions are needed, the user connects this external device to their smartphone, and the Wallet Instance communicates with it through the Secure Cryptographic Interface.
The primary security advantage comes from this physical separation, which isolates cryptographic operations from potential vulnerabilities in the smartphone’s general operating system.
Implementation considerations for organizations
For organizations implementing this approach, you’ll need to manage the distribution of physical hardware to your users. This involves procurement, personalization, distribution logistics, and ongoing support for lost or damaged devices.
Organizations with existing physical ID infrastructure may find this approach aligns well with their current operations. The hardware distribution adds costs and logistical complexity but provides a high level of security assurance through physical isolation.
For users, this solution requires carrying and connecting an additional device when using digital identity functions. While this adds a step to the process, it also provides visible security that some users find reassuring.
Benefits for organizations:
- High security through physical isolation
- Independence from smartphone security features
- Visible security that users can understand
- Protection of credentials even if the smartphone is compromised
Implementation challenges:
- Hardware distribution logistics and costs
- More complex recovery procedures when devices are lost
- Limited ability to perform remote updates
- Additional user friction in the authentication process
2. Digital identity on smartphone secure elements (Local WSCD/WSCA – platform: OEM Native SE)
This implementation leverages security features built into modern smartphones by device manufacturers, such as Apple’s Secure Element and Samsung Knox.
How the technology works
Premium smartphones contain built-in hardware security modules that can serve as the Wallet Secure Cryptographic Device (WSCD). These secure elements are integrated by the Original Equipment Manufacturer (OEM) and provide isolated environments for storing sensitive data and performing cryptographic operations.
Your wallet application interfaces with these secure elements through APIs provided by the phone manufacturer. Both the secure environment (WSCD) and the cryptographic application (WSCA) reside within the smartphone’s security architecture.
Implementation considerations for organizations
This approach eliminates the need to distribute physical hardware, as it uses security features already present in users’ devices. However, these features are typically only available in mid-range to premium smartphones, which limits the devices your solution can support.
Your development team will need to work with each platform’s specific security frameworks, potentially requiring different implementations for various manufacturers. This increases development complexity but removes the logistics of hardware distribution.
Strengths for organizations:
- No physical hardware to distribute
- Seamless user experience integrated with the smartphone
- Strong security through hardware isolation within the device
- Good integration with device biometric authentication
Limitations for organizations:
- Limited to users with compatible premium devices
- Different implementation requirements across phone manufacturers
- Creates potential exclusion of users with older or budget devices
- Requires adapting to each platform’s security framework
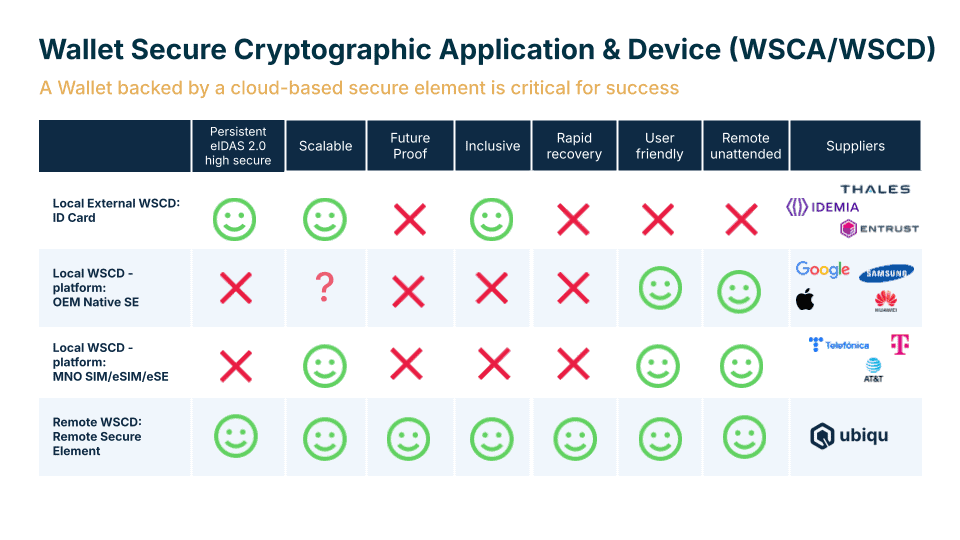
3. Digital identity on SIM cards or eSIMs (Local WSCD/WSCA Mobile-integrated)
This implementation utilizes the security features of SIM cards or embedded SIMs (eSIMs) in mobile phones as the secure element for digital identity.
How the technology works
SIM cards contain secure microprocessors that can function as the Wallet Secure Cryptographic Device (WSCD). The implementation can use:
- Physical SIM cards provided by mobile operators
- eSIM solutions embedded in smartphones
- Embedded Secure Elements (eSE) similar to SIMs
The wallet application communicates with these secure elements to perform cryptographic operations, with the WSCA running within the SIM environment.
Implementation considerations for organizations
This approach typically involves working with mobile network operators or eSIM providers to deploy your security solution. For physical SIMs, you’ll need partnerships with telecom providers to make your solution available to their subscribers.
The eSIM approach offers more flexibility but still requires integration with eSIM infrastructure. This eliminates physical hardware distribution but introduces dependencies on mobile operators or eSIM providers.
Strengths for organizations:
- Works with many types of mobile devices
- No separate hardware device for users to carry
- Builds on existing mobile infrastructure
- More inclusive than OEM-specific approaches
Limitations for organizations:
- Depends on partnerships with telecom providers
- Different implementation requirements across operators
- May tie users to specific mobile networks
- Potential complications when users change providers
4. Digital identity on cloud-based remote secure elements (Remote WSCD/WSCA)
This implementation places the secure element in data centers rather than on users’ devices, creating a remote connection between the wallet app and the security infrastructure.
How the technology works
In this approach, Hardware Security Modules (HSMs) in secure data centers serve as the Wallet Secure Cryptographic Device (WSCD). The Wallet Secure Cryptographic Application (WSCA) runs in this protected environment, and the wallet app on the user’s phone connects to it securely over the network.
The user’s credentials and private keys remain stored in the data center rather than on their device. When cryptographic operations are needed, the wallet app communicates with the remote secure element through encrypted channels.
Implementation considerations for organizations
This approach eliminates hardware dependencies on users’ devices, allowing your solution to work on virtually any smartphone with internet connectivity. Instead of managing distributed hardware, you focus on securing centralized infrastructure.
For implementation, you’ll need to establish secure communication between the wallet app and your data center infrastructure. You’ll also need to ensure appropriate data center security and availability.
Strengths for organizations:
- Works on nearly any smartphone, regardless of hardware capabilities
- No physical hardware distribution required
- Simplified credential recovery when users lose their phones
- Centralized security management
- More inclusive solution for all user demographics
Limitations for organizations:
- Requires network connectivity for cryptographic operations
- Needs robust data center security infrastructure
- Requires well-designed remote authentication
- May face initial user concerns about remote storage
This approach is particularly emphasized by Ubiqu, which has positioned its solution around the benefits of remote secure elements for scalability and inclusivity.
Why Ubiqu bets on the Remote Secure Element
The remote secure element approach is gaining attention because it addresses several practical challenges that organizations face when implementing digital identity solutions at scale.
Ubiqu, a company focusing on digital identity solutions, has built its technology around the remote secure element model. By placing secure elements in Google’s data centers or client-specific data centers, their solution creates a direct connection between mobile devices and remote hardware security modules.
As Guus Stigter, co-founder of Ubiqu, explains: “We saw that each traditional approach had significant drawbacks. External tokens aren’t user-friendly, OEM solutions limit you to premium phones, and SIM-based solutions often tie you to specific telecoms. Our Remote Secure Element solves all of these challenges – when you lose your phone, you haven’t lost your whole digital life because your encryption keys remain securely stored in the data center. This means recovery is simple, the solution is scalable, and it works on any device while maintaining the highest security standards.”
The remote approach particularly helps with credential recovery, as the digital identity remains intact in the data center even when a user’s phone is lost or damaged. This simplifies one of the most challenging aspects of digital identity management.