The European Digital Identity Wallet (EUDI Wallet) is a central pillar of eIDAS 2.0. Its purpose is to provide every EU citizen a secure and privacy-preserving way to manage their identity and official credentials online. But the Wallet is not just another app. It is a regulated trust service that must meet strict legal, technical, and interoperability requirements.
At the core of the Wallet is the idea of a trust chain. Every organization must be able to rely on the other, so that users can be confident that potential hacks or compromises are detected early. Before one step is confirmed, the next cannot begin.
Still, many organizations in our industry underestimate what this means in practice. That is understandable, because the legal and technical requirements are complex. But it makes it even more important to get the basics right. Trust cannot come from branding or user experience. It comes from a chain of verifiable guarantees, where each link depends on the previous one. In this article, I will walk through the key roles in that chain and explain why every organization needs to be clear about its own position and strategy.
What is the EUDI Wallet?
At its most basic level, the EUDI Wallet is a digital container that allows individuals to store and share verified information about themselves. This can include their name, date of birth, driving licence, university diplomas, health insurance status, or even login credentials for accessing public or private services. The Wallet allows people to prove their identity online and offline, sign documents with qualified electronic signatures, and selectively disclose attributes about themselves, depending on the context.
The wallet must meet a high bar for privacy and security. Citizens must be in control of their data and must be able to see who requested it, for what purpose, and on what legal basis. Every operation, from signing to authentication to data sharing, must happen with user consent and in line with GDPR and eIDAS rules.
The Architecture and Reference Framework: a great start, but difficult to decipher
The European Commission’s Architecture and Reference Framework (ARF) sets the rules for how the EUDI Wallet ecosystem should work. It is a comprehensive document that defines not only the technical requirements, but also the legal and organizational obligations for every actor in the chain. For policymakers and engineers, it is the official blueprint.
Yet for many organizations, the ARF is not easy to navigate. It is detailed, complex, and written in a way that requires deep familiarity with both regulation and technology. What often gets lost is the bigger picture: the ARF is not just about technical specifications, it is about clarifying the roles and responsibilities that make up the trust ecosystem.
Understanding those roles is critical. Every participant – from wallet providers to attribute issuers – needs to see where it fits in the framework and what that means for its strategy, technology choices, and compliance journey.
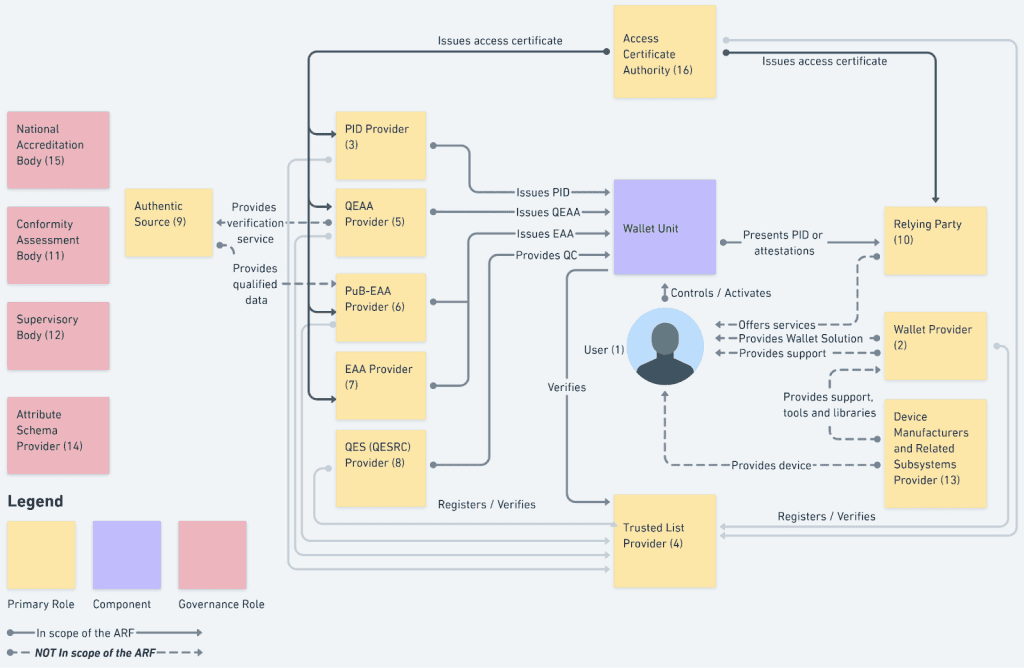
Figure 1 from the Architecture and Reference Framework, which provides an overview of the EUDI Wallet roles.
The Wallet Provider and the secure element as trust anchor
The Wallet provider is the first link in the trust chain. Their role is to ensure that the Wallet is not just functional, but genuinely trustworthy. This requires building on a certified secure element that protects the cryptographic keys and prevents tampering. Without that foundation, none of the later attestations in the chain hold any value.
There are different ways to implement a secure element, each with its own benefits and trade-offs. From hardware-based solutions to remote secure elements, Wallet providers must choose the right approach for their strategy and compliance path. In a recent article, we compared the 4 main Wallet secure cryptographic device application options in detail.
Once the secure element is in place and compliance requirements are confirmed through audits, the Wallet provider can issue what is called a Wallet unit attestation. Technically, this is a cryptographic certificate of authenticity for the Wallet instance. The secure element generates a unique key pair, with the private key stored securely inside the element: it will never be exposed. The Wallet provider then issues a signed statement proving that this key pair was created inside a certified secure element that meets eIDAS 2.0 requirements. Other parties can verify this statement against the Wallet provider’s certificate chain.
This Wallet unit attestation is the formal proof that the Wallet is genuine, its cryptographic keys are securely bound, and it complies with European certification standards. It is the technical handshake that allows the next step in the trust chain to begin.
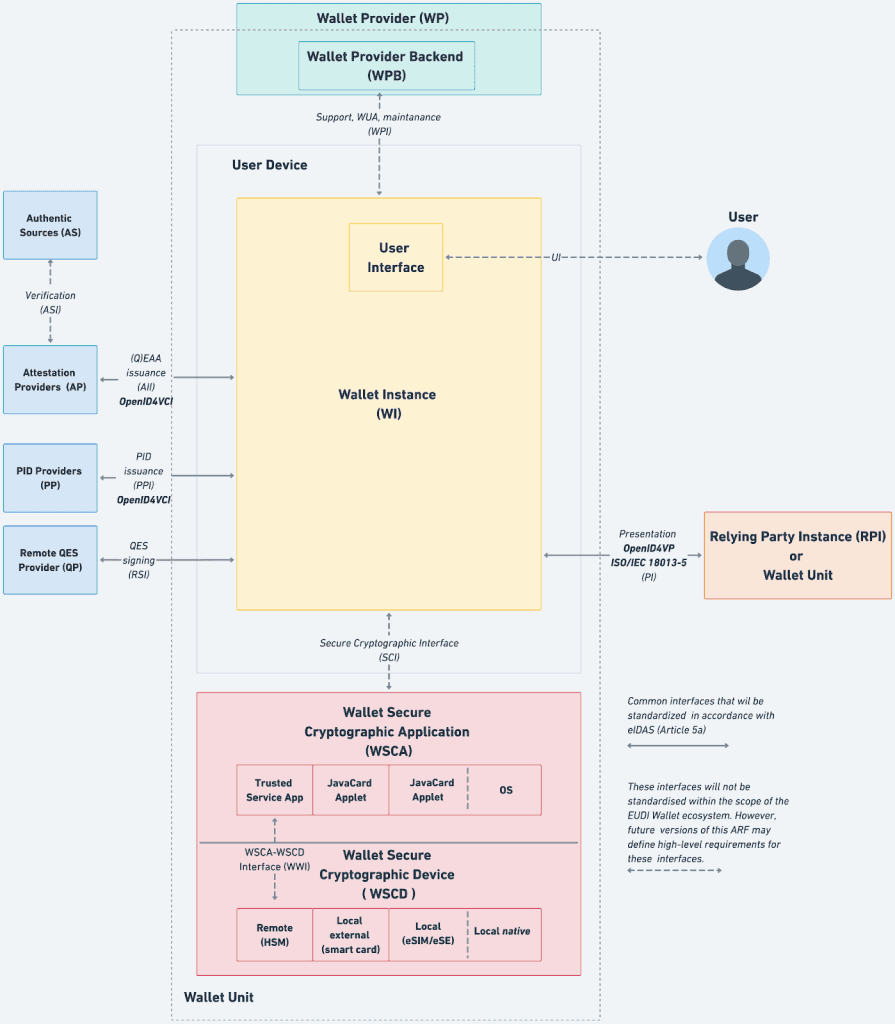
Figure 2 from the Architecture and Reference Framework, which displays the EUDI Wallet Solution reference architecture.
The PID Provider and identity verification
Once the Wallet is proven genuine through its Wallet unit attestation, the next step in the trust chain is the PID provider. PID stands for Personal Identification Data, and the provider is usually a national authority. Their responsibility is twofold, because the process requires both a Registration Authority (RA) and a Certification Authority (CA).
As RA, the role is to verify the user’s identity. This can involve checking physical documents, validating biometrics, and cross-referencing official registries. This step is not optional – it is the basis for binding any digital identity to a real-world person.
Once the identity is verified, the CA issues a PID attestation. This is a signed statement that binds the verified identity data to a specific public key, generated inside the Wallet’s secure element. Crucially, the CA also checks that the Wallet unit attestation is valid. That ensures the identity is not just linked to a real person, but also to a certified, trusted Wallet.
In technical terms, RA and CA are standard roles from Public Key Infrastructure (PKI). They are not mysterious new authorities, but IT functions that define who checks the person (RA) and who signs the credential (CA). These roles can be combined in one organization, but they can also be distributed across different providers, as long as both steps are completed and recognized in the trust chain.
If either element is missing – a verified person or a certified Wallet – the PID attestation cannot be issued. Both must be present, both must be trustworthy, and both must be verifiable. Only then can the digital identity exist as part of the trust chain.
Attribute Providers as the key to real-world usefulness
With a verified PID in place, the Wallet can now receive additional credentials from attribute providers. These are official entities listed on the EU Trusted List, such as universities, driver’s license authorities, or medical institutions. Their role is to enrich the Wallet with certified attributes that go beyond the core identity.
But not every organization can directly issue these credentials. To ensure trust across the EU, attribute issuance must be handled by or through a Qualified Trust Service Provider (QTSP) that is listed on the EU Trusted List. Becoming a QTSP is not trivial: it requires rigorous audits, certified technology, continuous monitoring, and significant investment. Many organizations, like universities or hospitals, may therefore choose to work with an established QTSP that manages the technical and compliance aspects for them.
Before issuing any credential, the QTSP always checks the basics of the trust chain: it validates the user’s verified PID and the Wallet unit attestation. Only if both are in order can an attribute be issued. Technically, this results in a cryptographically signed credential that binds a specific attribute (for example, “this person holds a master’s degree” or “this person is licensed to drive”) to the user’s Wallet key pair.
This stage transforms the Wallet from a verified identity container into a powerful tool for everyday life. It allows users to carry diplomas, licenses, and medical documents in a form that is portable, secure, and universally trusted across the EU.
Qualified Electronic Signatures: making digital binding
Once a Wallet contains a verified PID and trusted attributes, it can be used not just to prove identity but also to perform actions: the most important of which is to sign documents. This is where Qualified Electronic Signature (QES) Providers enter the trust chain. A QES has the same legal value as a handwritten signature before a notary, which is why this step is critical for enabling real-world transactions.
The QES provider, too, begins by checking that the Wallet unit attestation and PID attestation are valid, confirming that the user’s identity is trusted and bound to a certified Wallet. Only at that point, the provider will certify a signing key pair that is generated inside the Wallet’s secure element. The private key never leaves the secure element, while the public key is certified as belonging to the verified individual.
When the user signs a document, the Wallet applies the private key to create the signature. Anyone receiving the document can then validate it against the QES provider’s certificate chain. This proves three things at once: the signature was created by the verified person, the key is bound to a certified Wallet, and the signature has full legal validity under eIDAS 2.0.
This step transforms the Wallet from a trusted identity container into an active instrument for binding agreements. It enables contracts, financial deals, and government authorizations to be executed entirely online with the same assurance as if a notary had overseen the process.
Relying Parties: where trust meets reality
The last step in the trust chain is the relying party. These are the organizations that consume the credentials, signatures, and attestations provided by the Wallet – banks opening new accounts, airlines verifying passengers, universities checking diplomas, or government agencies granting access to services.
For relying parties, the strength of the Wallet lies in the fact that every step up to this point has already been verified. They do not have to individually check whether an ID card is genuine, whether a diploma has been forged, or whether a digital signature is valid. Instead, they can trust the certified chain of verifications: the Wallet unit attestation, the PID attestation, the attribute attestations, and the QES.
Technically, this works because each credential in the Wallet is cryptographically signed and linked to the EU Trusted List. A relying party can validate these signatures automatically against the trust framework. What they receive is not just a piece of information, but a verifiable proof that it comes from a trusted source, issued under European rules, and bound to a certified Wallet.
This is where the value of the EUDI Wallet becomes tangible. For users, it means seamless access to services across borders. For relying parties, it means they can operate with confidence, knowing that identity proofs, attributes, and signatures all carry legal weight and technical assurance. The Wallet only works if relying parties accept it – and they will only accept it if every link in the trust chain holds.
Why it all comes back to the secure element
Every link in the trust chain depends on the secure generation, storage, and use of cryptographic keys. That is exactly what the secure element is designed to provide. Whether it is embedded in the device or implemented as a Remote Secure Element, the purpose is the same: to ensure that even if the phone itself is compromised, the identity keys remain protected.
No secure element means no secure key. No secure key means no qualified signature. And no qualified signature means the Wallet cannot be trusted. If the foundation is weak, it does not matter how sophisticated the rest of the architecture may be – the legal value of the Wallet collapses.
At Ubiqu, we provide a certified Remote Secure Element that removes the hardware dependency while keeping the same level of assurance. It acts as a scalable trust anchor for Wallet providers and governments, enabling them to meet eIDAS 2.0 requirements without being tied to device-specific hardware. By getting the lowest layer right, the entire trust chain can operate as intended.
Back to the past, with modern assurance
In many ways, the EUDI Wallet takes us back to the past. There was a time when individuals themselves controlled what information to share with authorities or institutions. You filled out your tax declaration, added a photocopy of your passport, and sent it off. The responsibility for sharing data was yours.
The Wallet restores that principle, but with one major difference: today, every step can be verified. Instead of relying on paper copies and manual checks, the trust chain ensures that the Wallet is genuine, the identity is verified, the attributes are certified, and the signatures are legally valid. Users once again decide what to share and with whom – but now, organizations can trust that what is shared is authentic, secure, and compliant.
That is the power of the trust chain. It is not just a technical architecture, but a way to bring user control and institutional trust back together in the digital age.


