“We can’t wait for the iPhone 27 to be compliant.” With that remark, Boris Goranov, CEO of Ubiqu, cut straight to the point during last week’s technical webinar on eIDAS 2.0. While it’s tempting to assume that future smartphone models will eventually meet the security requirements for digital identity wallets, regulatory deadlines won’t wait. The eIDAS 2.0 framework is already in motion and by 2026, member states must have fully functional, compliant solutions in place.
But current smartphone hardware isn’t compliant. Secure elements in today’s devices aren’t certified to the required level and aren’t under user control; two non-negotiable conditions under the regulation. That means governments and wallet providers need to look beyond consumer hardware timelines and start building with infrastructure that meets the standard now.
In the webinar, Boris unpacked the technical architecture of eIDAS 2.0, clarified misconceptions about hardware readiness, and laid out the options organizations have if they want to deliver secure, compliant digital wallets in time.
Rethinking wallets as data pipes
Boris introduced a conceptual shift: viewing digital wallets as data pipes rather than storage devices. This perspective change helps explain the architectural differences between eIDAS 1.0 and eIDAS 2.0.
In traditional federated identity architectures, organizations establish direct connections with each other, creating what Boris described as “spaghetti”: a complex web of point-to-point relationships that scales quadratically as participants increase. When centralization emerged as a solution, it created new problems: once relying parties gain access to federated networks, they potentially access entire issuer databases rather than specific required data.
The Netherlands’ BKR (Bureau Krediet Registratie) mortgage system illustrates this challenge. All lenders must access a centralized credit registry where membership approval grants potential access to comprehensive financial data about any individual – far beyond what’s actually needed for specific transactions. This broad access forces strict membership controls and creates closed ecosystems where different sectors maintain separate federation networks rather than risk exposing sensitive data.
Digital wallets will change this dynamic. When viewed as data pipes, they enable direct issuer-to-verifier data flow through user-controlled transport, eliminating the need for organizations to know each other or maintain complex contractual relationships. The scope of each exchange becomes precisely defined: one user, one credential, one transaction.
The Architecture Reference Framework ecosystem
Before diving into technical challenges, Boris walked through the EU’s Architecture Reference Framework (ARF) to establish how different actors interact within the eIDAS 2.0 ecosystem. To grasp why the transition from centralized to user-controlled systems requires careful coordination, it’s important to understand the different roles in the ecosystem.
The framework establishes several key actors, each with specific responsibilities. Certificate authorities provide digital identities to all entities in the ecosystem through access certificates, enabling wallets to recognize trusted issuers and allowing users to know exactly who they’re receiving data from and sharing it with. The process involves registration authorities verifying identities and roles, checking that private keys are stored securely, then working with certificate authorities to issue and manage certificates.
Wallet issuers play a critical role by ensuring wallet quality and compliance. They verify that wallets aren’t compromised, confirm connection to certified secure cryptographic storage, and validate that keys are stored in certified hardware before issuing wallet unit attestations.
Personal Identity Data (PID) issuers, typically government organizations, establish user identity at high assurance levels by checking both the certified wallet and citizen database records before issuing digital identity credentials.
Qualified Electronic Attribute Attestation (QEAA) issuers then build on this foundation, verifying the government-issued PID and certified wallet before checking their authentic sources to issue specific credentials, such as driver’s licenses or diplomas. Finally, Qualified Electronic Signature (QES) providers enable users to digitally sign documents using their PID and wallet, requiring explicit user authorization before signing and delivering signed documents.
This interconnected cycle creates reusable trust anchors where each verification strengthens the overall ecosystem security.
The required hardware organizations need to understand
At the basis of the EUDI Wallet lies hardware; secure elements. The ARF describes four main Wallet Secure Cryptographic Device and Application options. The hardware in smartphones is one of these options, but Boris explained why they don’t meet eIDAS 2.0 security requirements, addressing a common misconception among organizations planning digital wallet implementations. The latest iPhones, Samsung Galaxy phones, and Google Pixels weren’t designed for the specific regulatory requirements that eIDAS 2.0 demands.
Current smartphones contain secure elements. However, these chips are neither certified to the security level eIDAS high demands, nor do they operate under user control: they operate under platform control. For eIDAS 2.0 compliance, users must have sole control of their cryptographic keys stored in certified hardware.
Even if Apple and Google were to decide tomorrow to build compliant, secure elements, market penetration would still take years. Organizations planning eIDAS 2.0 implementations in 2025-2026 cannot wait for the iPhone 27 to potentially offer compliance.
Boris demonstrated why secure elements are essential through a technical explanation of voltage manipulation attacks. By controlling processor voltage during security checks, sophisticated attackers can cause regular processors to produce random calculation results instead of proper verification. Under optimal conditions, dedicated attackers require approximately 1.2 million seconds, or about two weeks, to compromise any regular processor without specialized protections. Only certified secure elements have built-in defenses against these attack vectors, which is why eIDAS 2.0 mandates their use rather than allowing regular smartphone processors.
The implications extend beyond the security of individual devices. If attackers compromise these processors, they gain access to private keys, can forge digital signatures, and potentially undermine entire digital identity ecosystems. A single compromised device could invalidate trust in thousands of credentials and transactions, creating compliance failures and legal liability for organizations across the ecosystem.
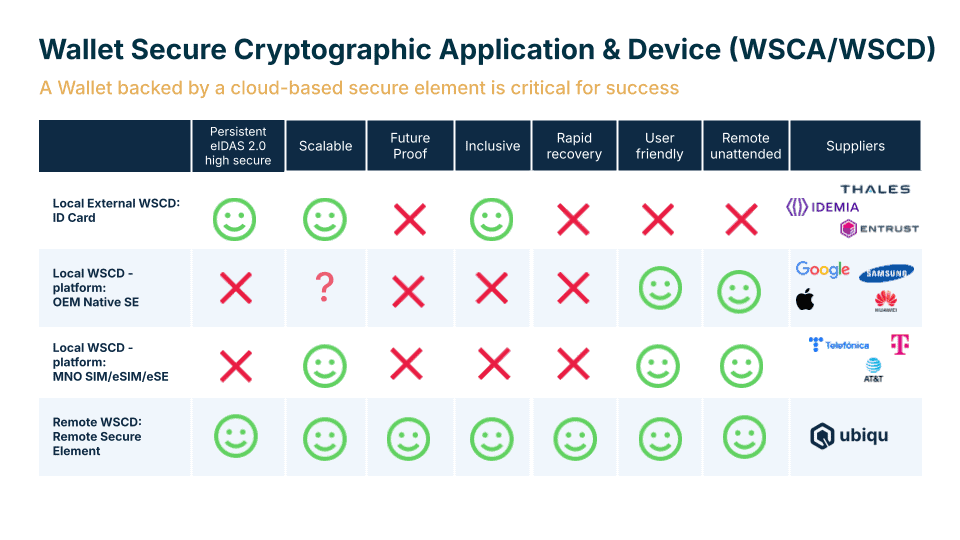
The gap between regulation and current technology
The disconnect between eIDAS 2.0 requirements and current market capabilities represents more than a temporary inconvenience – it’s a mismatch between regulatory expectations and technological availability. This gap forces organizations to choose between waiting years for the technology ecosystem to mature or finding innovative solutions that work with today’s infrastructure while meeting regulatory security standards.
Boris outlined four potential approaches to secure cryptographic storage: traditional identity cards, native smartphone storage, SIM card solutions, and remote secure elements. Each presents distinct trade-offs between security, scalability, inclusivity, and user experience.
Physical solutions like identity cards offer proven security but sacrifice user convenience and remote activation capabilities. Native smartphone storage provides excellent user experience but lacks regulatory compliance. SIM card approaches face similar certification challenges while introducing complex telecom dependencies.
Physical secure elements also face an inherent vulnerability that many organizations overlook: when hardware vulnerabilities are discovered, complete replacement becomes necessary at massive scale. Estonia’s experience replacing 730,000 SIM cards when security flaws were found illustrates this challenge. Unlike software vulnerabilities that can be patched remotely, hardware compromises require physical replacement of every affected device, creating logistical challenges and service disruptions.
Remote secure elements emerge as a potential bridge between current capabilities and future requirements. By maintaining certified hardware under user control while working with existing devices, this approach enables immediate compliance without waiting for hardware manufacturer upgrades or massive device replacement programs.
QTSP acceleration as ecosystem enabler
The webinar revealed another critical bottleneck in eIDAS 2.0 adoption: the time and cost required for organizations to become Qualified Trust Service Providers. Traditional QTSP certification requires demonstrating effectiveness across more than 1,500 compliance line items, typically taking 2-3 years and costing millions of euros. This timeline conflicts with the urgency many organizations feel to implement digital identity solutions.
Boris explained how Ubiqu’s pre-certified QTSP platform can compress this timeline to three months by automating technical compliance requirements. Rather than each organization building cryptographic infrastructure, operational environments, and DevOps processes from scratch, they can leverage Ubiqu’s platform where 90% of technical compliance is already certified. This allows organizations to focus on governance, business processes, and organizational requirements while eliminating technical implementation risks.
This acceleration isn’t just about convenience – it’s about ecosystem viability. If becoming a QTSP remains a multi-year, high-risk endeavor, the number of qualified issuers will remain limited, constraining the entire ecosystem’s growth. Ubiqu’s platform can democratize QTSP status, enabling more organizations to participate as authentic data sources and expanding the utility of digital wallets for citizens and businesses.
The annual recertification requirements add another layer of complexity that Ubiqu’s automated platform helps manage. By maintaining continuous compliance monitoring and evidence collection, the platform reduces the ongoing burden of QTSP status while ensuring organizations remain audit-ready.
The path forward
The webinar presented digital identity at an inflection point. eIDAS 2.0 provides a regulatory framework that addresses long-standing issues in federated identity systems. The architecture is sound, the user experience greatly improved, and the trust model is more transparent. But the technology needed to make it all work, particularly at scale, is not yet present in the devices most people carry.
This disconnect creates both a sense of urgency and a corresponding responsibility. Many public authorities are proceeding with eIDAS 2.0 preparations under the assumption that current smartphone hardware will suffice. In practice, however, today’s devices do not meet the required security level: their secure elements are not certified for eIDAS high, nor are they under the sole control of the user. This is not a matter of delay, but of limited awareness. To meet the 2026 deadline, it is important that alternative, compliant solutions, such as remote secure elements, are actively explored now.
The question is no longer whether eIDAS 2.0 will transform digital identity – it will. The real question is how organizations will implement it: with theoretical compliance plans, or with production-ready architecture that can operate today.That’s where the Remote Secure Element comes in. Ubiqu’s RSE enables fully compliant, user-controlled key storage without waiting for next-generation hardware. It allows organizations to launch eIDAS 2.0 wallets on existing smartphones: securely, scalably, and in line with regulatory standards.


